CommonLit: What is it And How Does It Work?
CommonLit is a digital literacy platform that provides curriculum-aligned instruction and evaluations for learners. Designed to cater to a diverse student population, spanning from the 3rd to the 12th grade,…

How To Take A Screenshot On Dell Laptops And PCs
During the period prior to the advent of screenshot functionality, the concept of a straightforward tool that could effortlessly grab an exact representation of your display’s content was unimaginable. This…

How to Download Four Elements Trainer Mod APK v1.0.7c
Step into a realm where dreams merge with the tangible in the enchanting Four Elements Trainer Mod APK. Journey across the worlds of Avatar: The Last Airbender and The Legend…

Vanced Manager: How to Get This Android App and Install It
The Vanced Manager APK is a mobile application for Android that provides a means to acquire and set up different utilities and modifications for your Device. YouTube Vanced, which is…

What is Proxyium? Guide to Using A Free Web Proxy
Proxyium is your ultimate destination for online proxy services, aims to transform how you navigate the internet. Offering complimentary services for anonymous web surfing and lifting restrictions on websites, Proxyium…

What Does No Location Found Mean? (Easy Guide)
Greetings, my fantastic audience! In our discussion today, we’ll delve into the meaning of “No Location Found.” Ever found yourself peering at your smartphone, trying to pinpoint a buddy’s location…

Amazon.com/code: Stream Prime Video on Multiple Devices
Amazon.com/code: Amazon Prime Video is a well-regarded subscription-based streaming platform provided by amazon.com/code that features an extensive array of films, television series, and exclusive productions. Those who subscribe have the…
What is HDHub4U? Is It Safe to Watch Movies Online?
If you’re looking to fulfill your daily need for entertainment, it’s important to have the option to view your preferred movies in the language you want, and to be able…

Netwyman Blogs: A Comprehensive Guide to The Amazing World
Netwyman Blogs continues to shine as a beacon of insightful knowledge and engaging narratives amidst the ever-changing landscape of digital media. Stepping into the online conversations of 2024, the significance…
What is Cataz? How to Watch Movies And TV Series?
Lately, the growing trend of using streaming services Like Cataz worldwide has been significantly driven by the current Coronavirus outbreak. Individuals are turning to binge-watching online shows and films as…

What is Score808? Is it Safe to Watch Live Sports?
For the countless enthusiasts of soccer eager to catch every game of this thrilling sport, we’ve got some great news. Introducing a comprehensive platform that encapsulates all things Football, where…

Wmlink/2step: Enable Maximum Online Account Security
In today’s digital era, safeguarding our internet-based accounts has become extremely important. As the risks of cyber attacks and unauthorized data access continue to rise, it is essential to safeguard…
![Create Meme GIFs with Best 4 Meme GIF Generators [Quick Guide]](https://www.seventech.ai/wp-content/uploads/2024/04/how-to-make-meme-gif-355x199.jpg)
Create Meme GIFs with Best 4 Meme GIF Generators [Quick Guide]
In the digital age, memes have become a ubiquitous form of communication, offering a blend of humor, wit, and cultural relevance. Among the myriad meme formats, GIFs (Graphics Interchange Format)…

Overview of GPT4Free: A Complete Guide
One of the benefits of Artificial Intelligence is its adaptability. Regardless of the specific model, modifications can be made with ease if you possess the necessary knowledge to adjust it…
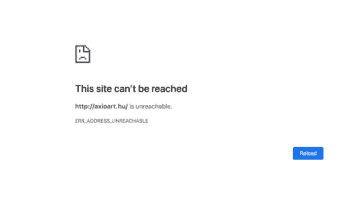
Err_Address_Unreachable: Best Methods for Fixing Error
Are you experiencing the “err_address_unreachable” message when attempting to visit a website? Rest assured, many others encounter this issue as well. This error, which happens for various reasons, has thankfully…
3 Things Any Brand New Investor Needs to Know
Investing has its jargon, its theories, and its strategies. All these add up to what seems like a high barrier to entry. Anyone looking from the outside in might be…